In my last blog, I explained the operating principle of a conventional access control system and how mobile credentials are replacing physical key cards in legacy systems. Mobile Access is, in fact, a very widely used term, and it has inherited slightly different meanings depending on the system in which it is used. In most cases, mobile access is referred to as a mobile credential for a conventional access control system, as explained in my latest article.
1. Cloud Service and mobile apps
When working with mobile apps, the essential requirement is usually a cloud service to which mobile phones can connect and exchange data.
Mobile apps mainly serve as components of a cloud service, offering users a mobile interface to the service. There is however a difference between actual (native) mobile applications and mobile web-based apps.
The web-based app – usually called just a web app- is not a real mobile app but rather an extension to the cloud service interface using the phone’s web browser to connect to the service.
However, whenever the app needs to carry out tasks that need to happen offline (without a continuous internet / cellular connection), like opening a door or a lock, a native mobile application is required.
Native mobile apps are software loaded onto a mobile phone, as software on laptops. They are usually freely available in Apple’s or Google’s application stores.
Once installed on the user’s mobile phone, the user can sign in to the application with the credentials provided by the cloud service and enjoy the features provided by the service provider.
A native application can interact with the phone’s advanced features and technologies like Bluetooth / NFC radios and location and utilize the phone’s higher levels of security to ensure high levels of security settings for mobile access control.
2. Cloud-based access control
Conventional access control systems are rarely cloud-based. They are usually installed on customer-specific servers and require specific communication channels (like VPN or other isolated connections) to access the server from the outside. This type of architecture dates back to when cloud computing and services were unavailable. Thus in my postings, I refer to these kinds of systems as legacy access control systems.
As explained earlier, introducing mobile IDs (mobile credentials) requires an actual cloud service where the credentials are managed and created. In combination with legacy access control systems, the cloud service connects to the access control via a specific API interface or another more manual method (like CSV import) to merge the mobile IDs with the users.
Thanks to cloud service development and advancements in cybersecurity during recent years, complete cloud-based access control systems have also gained popularity, offering higher flexibility, simplified user interface and more advanced features.
Customers globally are now rapidly adopting these new services that offer simplicity, flexibility and a constant flow of new features and applications at a competitive price.
3. ID-based keyless access control
Keyless access – a key feature in a cloud-based access control system – saves everyone’s time and money. Installing a mobile access control system often costs half the price of physical key card systems. Since adding and removing users happens digitally, you will save time not having to distribute keys to your tenants or employees manually.
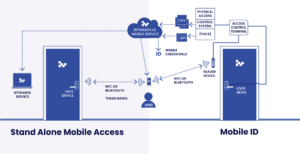
Normally a cloud-based access control system follows similar architecture as legacy systems in which the credentials are just simple IDs stored on the user’s RFID tag or a mobile phone (read more in my last article).
The trick in a keyless system is to update the locks with identical IDs as stored in the users’ phones. Matching IDs will allow the lock to open and grant access to the user.
To update the whitelist, (list of IDs that can open a lock), a hub acting as a router between the lock and the cloud service is required. Commonly the locks use a low-band wireless radio to connect to the hub. They also have a separate Bluetooth and NFC radio to communicate with the phones or RFID tags.
In most cases, the hub is connected wirelessly to the building’s Wi-Fi providing internet access and, finally, the connection to the cloud.
Mobile phones connect to the cloud and update their IDs through the cellular network.
Similarly, as in a legacy system, the keyless solution depends on a continuous network connection between the cloud and the hub and the lock.
4. Mobile-based access control
Bitwards has created and patented a mobile-based access control solution based on smart tokens managed and issued in a cloud access control service. The service distributes the tokens to users’ mobile phones allowing them to access the desired doors.
This mobile payment-related technology offers exceptional security and a true smart key allowing any user to open locks using Bluetooth or NFC on their mobile phones.
Unlike an ID-based access control system, this solution can operate with complete network independence. The system only needs smart locks at each door and does not require any additional hubs or hardware. The locks communicate with the phones using Bluetooth or NFC radio.
The tokens contain the needed information for complete lock control and user access management. The data in the tokens are exchanged with the locks when users open the locks with their mobile phones. This transaction happens within milliseconds and allows sharing of all required data between the lock and the cloud. The unique feature of smart tokens is that they also work when the phone is not connected to the cellular network, increasing the reliability and useability of the solution.
The data in the tokens may differ among the users. For example, a door may be opened for a prolonged period for slower access, or a shopkeeper’s token may turn off the alarm system when entering the shop after opening hours.
The tokens can also contain other data such as opening schedules for specific doors or access codes for locks that also have a pin pad available, allowing the use of access codes.
All end-users can use a single app to access any door at any customer or facility offering a truly multi-tenant and domain operation.
A true mobile-based access control combines high flexibility, simplicity and a low-cost system while offering a full-featured access control.
Conclusion – ID on Mobile vs Data on Mobile
When looking at both solutions – an ID-based and a mobile-based system from a higher perspective – one will notice a clear distinction in the complexity of the hardware architecture. A system loaded with more hardware will eventually cost more in terms of hardware, installation and maintenance costs. However, the main difference is in the system intelligence and the distribution to the access points.
A conventional system relies on constant network connection and hardware to distribute the access “intelligence” to the doors.
In a mobile-based system, this intelligence is packed into tokens shared to all system users’ phones which carry the intelligent data to the doors they want to access. The tokens and data may change depending on changes made in the cloud service by the system administrator.
A mobile-based system also relies on cloud connectivity sometimes but works asynchronously, offering total control when a network is unavailable. The only connection needed is the user’s cellular connection.
A mobile-based system offers customers and end-users a highly reliable, secure and usable solution with an overall low-cost investment.
Text: Eljas Saastamoinen, CEO, Bitwards